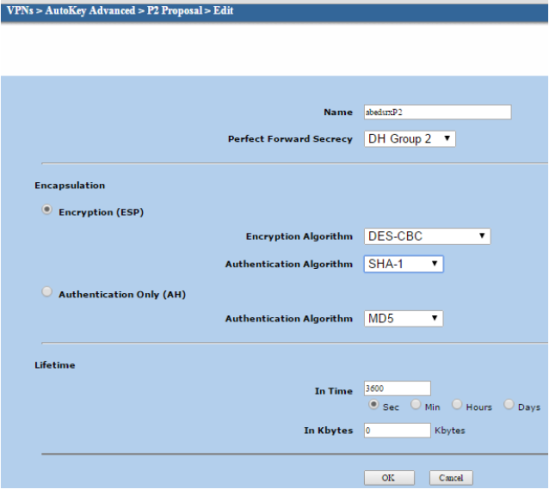
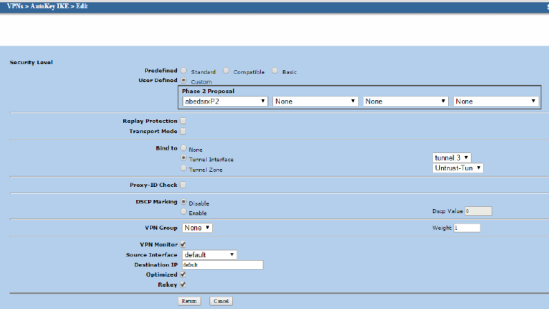
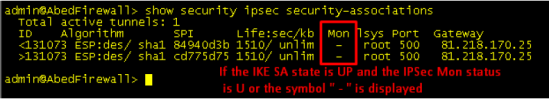
For VPN debugging, which enables logging to the KMD log by default without the need to commit:
>request security ike debug-enable local <ip-address> remote <ip-address> level <level>
and to turn off:
>request security ike debug-disable
Review logs written to /var/log/kmd:
> show log kmd
Checking the debug status:
> show security ike debug-status
For taking a tcpdump of an interface to analyze with Wireshark or similar (Hidden command):
>monitor traffic interface ge-0/0/1.0 write-file test.pcap
Can be viewed on the SRX also (Hidden command):
>monitor traffic read-file test.pcap
To see default config settings (Hidden command):
# show groups junos-defaults
>show configuration groups junos-defaults
>show configuration groups junos-defaults applications
To see some system limits:
>show log nsd_chk_only
To see currently working Junos applications definitions (Hidden command):
>request pfe execute command “show usp app-def tcp” target fwdd
>request pfe execute command “show usp app-def udp” target fwdd
If you dont have the root login and still you want to capture output on PFE withough going to vty mode. Here is the way:
>request pfe execute target fwdd command “show usp threads”<<<<Just add pfe commands in colun” “.
To make all daemons re-read the configuration. (Hidden command):
# commit full
Another hidden command useful when troubleshooting is:
> show chassis cluster information ?
Disabling UTM process (Hidden command):
admin@AbedFirewall# set system services utmd
^
syntax error.
admin@AbedFirewall# set system processes utmd disable
admin@AbedFirewall# show | compare
[edit system]
+ processes {
+ utmd disable;
+ }
admin@AbedFirewall# commit check
configuration check succeeds
ALG Configuration (hidden command):
run show security alg configuration
(sa instead of security-associations) (hidden command):
> show security ike sa
> show security ipsec sa
usefull in HA (hidden command):
root@SRX# run set chassis cluster control-link-vlan ?
Possible completions:
disable Disable control VLAN tag
enable Enable control VLAN tag
reboot Reboot the system after setting the identifiers
Another good one (hidden command):
admin@AbedFirewall> start shell pfe network fwdd
BSD platform (OCTEON processor, 416MB memory, 8192KB flash)
FLOWD_OCTEON(AbedFirewall vty)#
clear clear commands
connect connect to a remote TNP endpoint
debug Debug commands
diagnostic diagnostic commands
eth eth commands
jsflib jsf lib information
pconnect connect to a remote PIP endpoint
peekbyte display memory in bytes
peeklong display memory in 32bit longs
peekword display memory in 16bit words
plugin plugin information
pty open a pty to a PIC
quit quit TTY environment
reboot reboot hardware
set set system parameters
show show system information
sleep pause for a few seconds
test test commands
undebug Undebug commands
vty open a vty to a remote TNP endpoint
FLOWD_OCTEON(AbedFirewall vty)# show threads
PID PR State Name Stack Use Time (Last/Max/Total) cpu
— — ——- ——————— ——— ———————
1 H asleep Maintenance 1144/73824 0/8/45 ms 0%
2 L running Idle 2200/73824 0/8/5518829 ms 0%
3 H asleep Timer Services 2120/73824 0/8/43707 ms 0%
5 L asleep Ukern Syslog 856/73824 0/0/0 ms 0%
6 L asleep Sheaf Background 1128/73824 0/8/8662 ms 0%
7 M asleep mac_db 856/73824 0/0/0 ms 0%
8 M asleep Docsis 2152/73824 0/8/22701 ms 0%
…….
214 L asleep Virtual Console 2168/73824 0/0/0 ms 0%
FLOWD_OCTEON(AbedFirewall vty)# show threads 214
PID PR State Name Stack Use Time (Last/Max/Total) cpu
— — ——- ——————— ——— ———————
214 L asleep Virtual Console 2168/73824 0/0/0 ms 0%
Wakeups:
Type ID Enabled Pending Context
Timer 00 No No 0x489ab068
Socket 00 Yes No 0x5027f088
Frame 00: sp = 0x502ceb10, pc = 0x08014cb0
Frame 01: sp = 0x502ceb88, pc = 0x0801b9b4
Frame 02: sp = 0x502cebc0, pc = 0x08047ee4
Frame 03: sp = 0x502cebf0, pc = 0x08046df0
Frame 04: sp = 0x502cec10, pc = 0x086df254
Frame 05: sp = 0x502cec38, pc = 0x0802b8ec
Frame 06: sp = 0x502cec60, pc = 0x000001a0
FLOWD_OCTEON(AbedFirewall vty)#
To log in to other node of SRX cluster (Hidden command):
{primary:node0}
lab@E1> request routing-engine login ?
Possible completions:
<[Enter]> Execute this command
| Pipe through a command
{primary:node0}
lab@E1> request routing-engine login node 1
— JUNOS 12.1R3.5 built 2012-08-09 07:05:23 UTC
{secondary:node1}
lab@E2>
——————————————
# set apply-flags omit
——————————————
request pfe execute target fwdd command “sh usp ipsec sa”
——————————————
show pfe interfaces
show pfe interfaces statistics
——————————————
show tnp addresses
——————————————
To login to other High-End node:
{primary:node1}
user@SRX-node1> start shell
% rlogin -Jk -T node0
▒
— JUNOS 12.1X44-D40.2 built 2014-08-28 12:48:56 UTC
{secondary:node0}
user@SRX-node0>
And For fun 🙂
# run show version and haiku
Hostname: AbedFirewall
Model: srx210he
JUNOS Software Release [12.1X44-D45.2]
Nothing feels as good
Arms filled with wiggling children
So much hope and love
Good Luck 🙂
Shared by: Abed AL-R. Bishara
Source