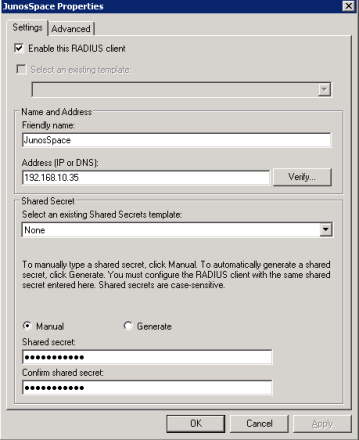
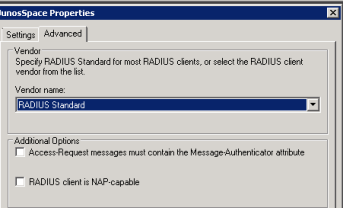
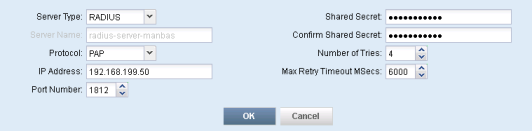
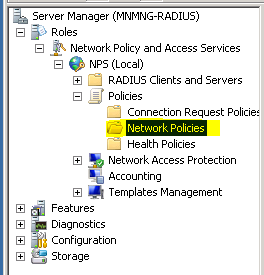
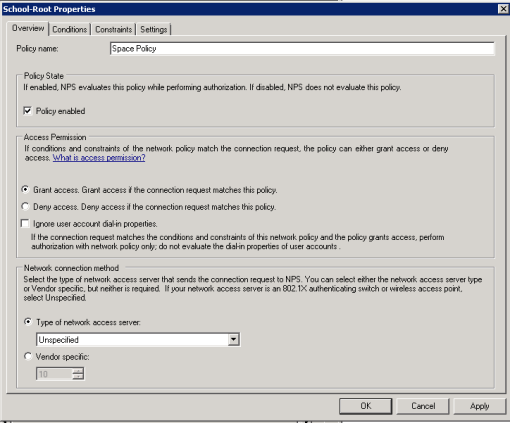
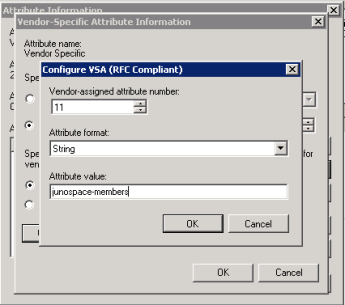
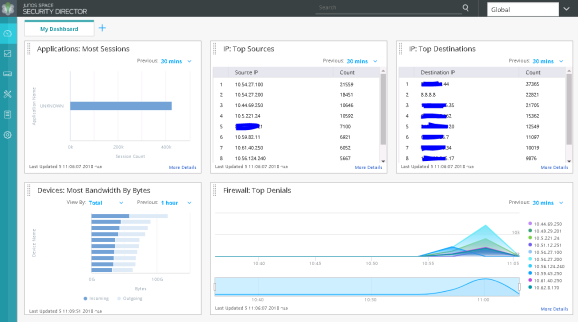
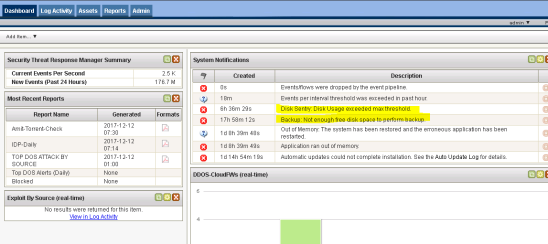
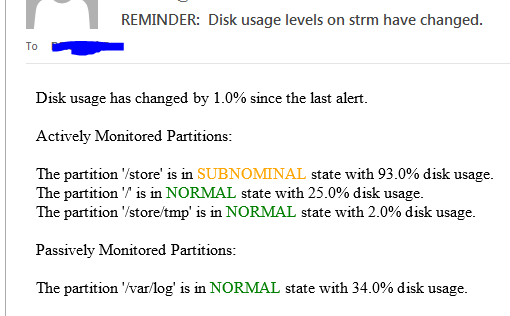
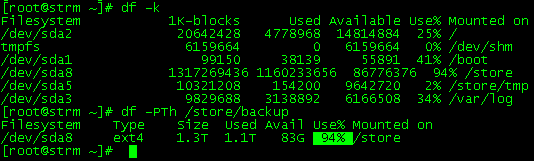
admin@SRX> ftp 172.16.1.17
Oct 18 14:36:55
Connected to 172.16.1.17.
220-FileZilla Server 0.9.60 beta
220-written by Tim Kosse (tim.kosse@filezilla-project.org)
220 Please visit https://filezilla-project.org/
Name (172.16.1.17:admin): <type here the username if not admin>
331 Password required for cloud
Password:
230 Logged on
Remote system type is UNIX.
ftp> put /var/tmp/Flow_PCAP.ge-0.0.4 Flow_PCAP.ge-0.0.4.zip
local: /var/tmp/Flow_PCAP.ge-0.0.4 remote: Flow_PCAP.ge-0.0.4.zip
200 Port command successful
150 Opening data channel for file upload to server of “/Flow_PCAP.ge-0.0.4.zip”
100% |**********************************************************************************************************************************************************| 12403 KB –:– ETAA
226 Successfully transferred “/Flow_PCAP.ge-0.0.4.zip”
12701026 bytes sent in 3.38 seconds (3.59 MB/s)
ftp> bye
221 Goodbye