First of all, There should two servers, SafeNet & LDAP/Radius server which is including all usernames and passwords. And SafeNet server should be configured to establish sync with LDAP/Radius server in order to pull out all usernames/password.
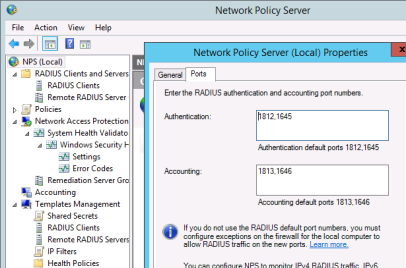
Second, check with which ports OTP is listening:
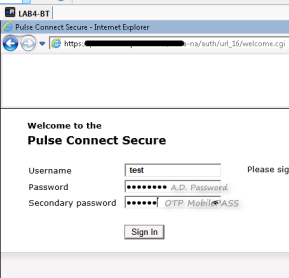
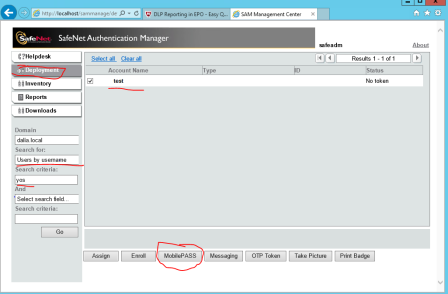
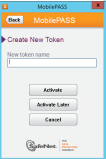
Now we should activate the username who’s going to establish the VPN connection via OTP .

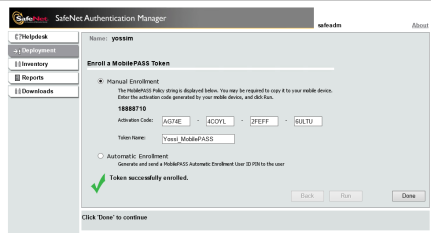
Now we need to type the activation code received by the application:
 >>
>>  >>
>>  >>
>> 
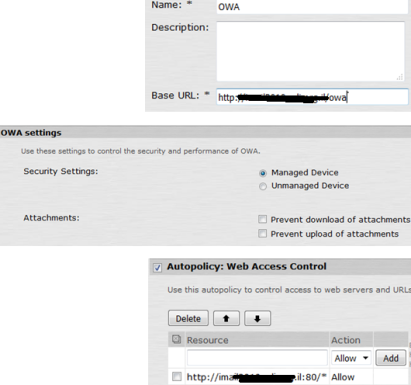
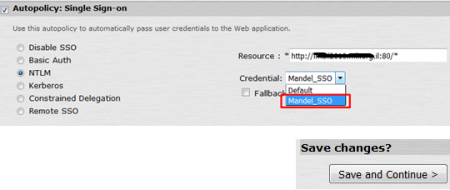
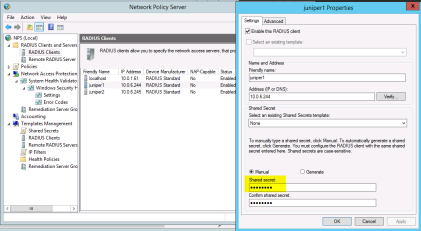
Now this is how to configure the OTP connection in the MAG:


- The shared secret is what you determine in the OTP server settings, e.g SafeNet
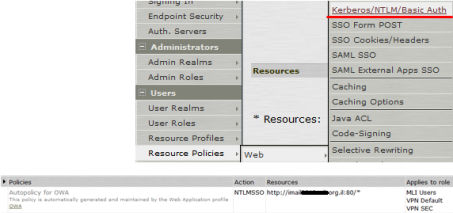
Now you configure realm with correct authentication methods:

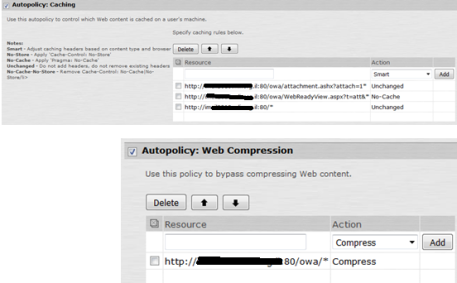
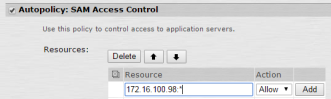
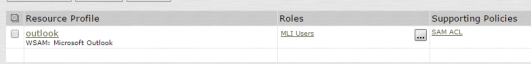
And all other roles and page policies …